
A federal court in Hammond, Indiana, unsealed an indictment on Tuesday charging Guan Tianfeng, a Chinese citizen, with conspiring to hack firewall devices globally in 2020, officials stated.
Guan and his associates, working at Sichuan Silence Information Technology Co. Ltd., exploited an unknown “zero-day” vulnerability in firewalls developed by Sophos Ltd., a U.K.-based cybersecurity company.
According to officials, the malware they created was designed to steal data and encrypt files if victims tried to remove the infection. Their operation compromised approximately 81,000 firewalls worldwide, including one used by a U.S. government agency.

“The defendant and his conspirators compromised tens of thousands of firewalls and then continued to hold at risk these devices, which protect computers in the United States and around the world,” said Assistant Attorney General for National Security Matthew G. Olsen. “The Department of Justice will hold accountable those who contribute to the dangerous ecosystem of China-based enabling companies that carry out indiscriminate hacks on behalf of their sponsors and undermine global cybersecurity.”
Defendants are presumed innocent unless proven guilty.
The Conspiracy to Exploit Common Vulnerabilities and Exposures (CVE) 2020-12271
 According to the indictment, Guan and his co-conspirators created, tested, and deployed malware in 2020 that exploited a zero-day vulnerability in Sophos firewalls, later identified as CVE-2020-12271. The attack targeted about 81,000 firewalls worldwide, including those in the Northern District of Indiana.
According to the indictment, Guan and his co-conspirators created, tested, and deployed malware in 2020 that exploited a zero-day vulnerability in Sophos firewalls, later identified as CVE-2020-12271. The attack targeted about 81,000 firewalls worldwide, including those in the Northern District of Indiana.
The malware was designed to steal data from the firewalls. To disguise their actions, the group used fake domains resembling legitimate Sophos domains, such as sophosfirewallupdate.com. Sophos quickly identified the breach and secured its customers’ firewalls within two days. In response, the conspirators modified their malware to include ransomware that encrypted files if removal was attempted. Although the encryption failed, their actions showed a blatant disregard for the damage they could inflict on victims.
Guan Tianfeng’s Employment and Sichuan Silence’s Relationship with the PRC Government
Soon after the Sophos announcements in October, the FBI issued a call for information regarding computer intrusions into Sophos edge devices.
The FBI continues to solicit information on PRC-sponsored malicious actors targeting edge devices and network security appliances.
The U.S. Department of State also announced rewards today of up to $10 million for information leading to the identification or location of Guan or any person who, while acting at the direction or under the control of a foreign government, engages in certain malicious cyber activities against U.S. critical infrastructure in violation of the Computer Fraud and Abuse Act.
The U.S. Department of the Treasury’s Office of Foreign Assets Control also announced sanctions on Sichuan Silence and Guan.
Trial Attorneys Jacques Singer-Emery and George Brown of the National Security Division’s National Security Cyber Section and Assistant U.S. Attorney Steven J. Lupa for the Northern District of Indiana are prosecuting the case.
The FBI continues to investigate Sichuan Silence’s hacking activities and intrusions into various edge devices.
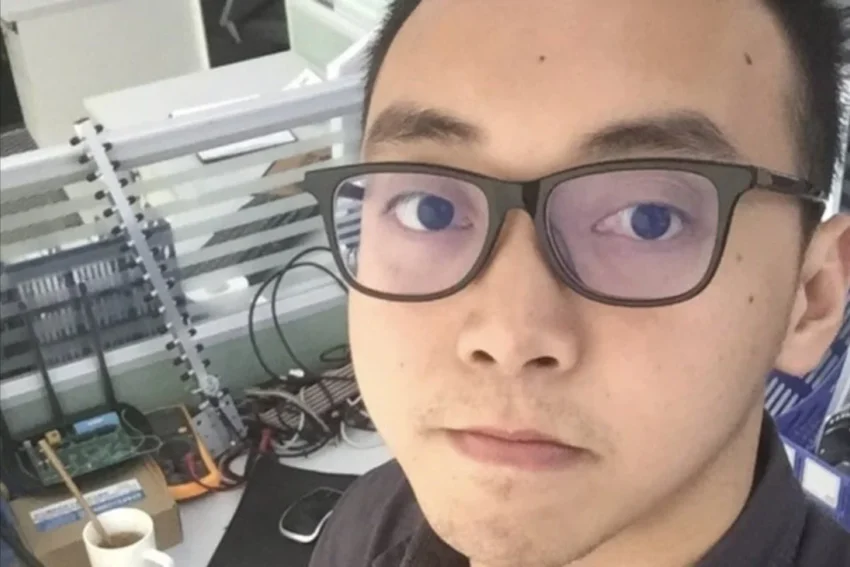
 Court documents reveal that Guan worked for Sichuan Silence, a China-based private company that has provided services to the PRC Ministry of Public Security and other government organizations. According to its website, Sichuan Silence developed tools to scan and identify overseas network targets for intelligence gathering.
Court documents reveal that Guan worked for Sichuan Silence, a China-based private company that has provided services to the PRC Ministry of Public Security and other government organizations. According to its website, Sichuan Silence developed tools to scan and identify overseas network targets for intelligence gathering.